Get ATO protection with zero false positives and no added friction to the user experience.
Ready to stop researching and start trying?
Get Started for FreeAccount takeover (ATO) and credential stuffing attacks are rapidly increasing due to the ease in which customer accounts can by hijacked using credentials breached on other sites
Studies show total fraud incident costs are twice the cost of the fraud itself. Regardless of the size, consumers blame the brand, lose confidence, and often take their business elsewhere.
Enzoic checks every login to identify and block access using known compromised credentials, an approach previously prohibitive to all but the largest organizations.
OVERVIEW
Our ATO protection is an innovative API solution that allows you to securely compare user credentials against a continuously updated database of compromised credentials.
Once an exposure is discovered, you can force a password reset, restrict access or take some other action. This occurs in real-time during user login, account set-up or password reset.
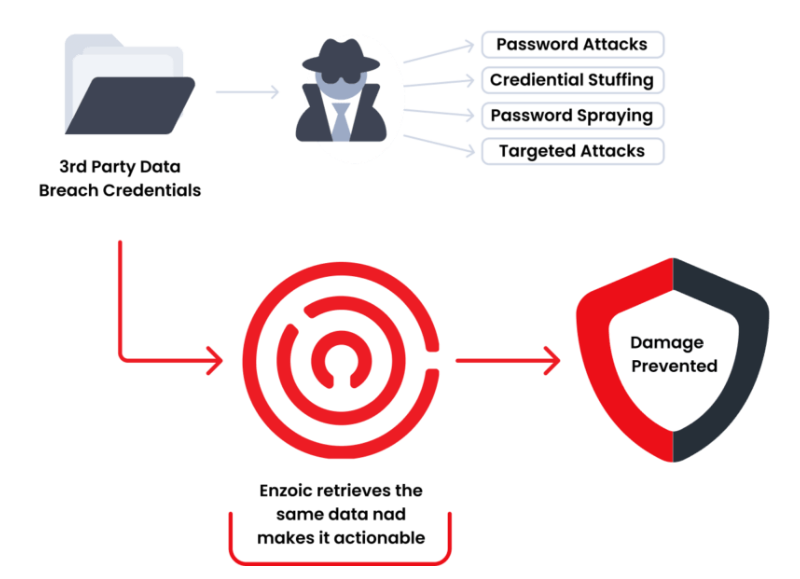
HOW IT WORKS
Checking the validity of usernames and passwords isn’t enough to determine if the credentials being used on your site were compromised in a third-party data breach.
Call Enzoic’s enterprise REST API in the background to determine if the credentials are available to cybercriminals on the dark web.
If compromised: step-up authentication, reset the password, reduce privileges or use other threat mitigation tactics.
Enzoic’s APIs allow you to eliminate the threat from compromised credentials on your site or web app.
Resource Hub
Read how to battle account takeover risks. Start cross-checking current credentials without adding friction to the user experience.
Resource Hub
Read this e-Book to discover the four ways to safeguard your organization with a robust password policy.
Blog
All enterprises balance their need for strong authentication security against a frictionless user login process. How some solutions can help that balance.
Enzoic closes the obvious and unacceptable risk of allowing known compromised credentials to be used on your site. Our solution is the simplest and most cost-effective way to harden the password layer in your overall security architecture.
The most common targets for ATO and account hijacking are sites that hold access to value within the individual account (e.g. ability to transfer funds, obtain products / services, access to redeem loyalty points, or personal information that can be resold on the black market).
Maintaining our compromised credential database is fundamental to our business model. Our database contains multiple billions of carefully indexed records and is continuously updated through automation and by our threat analyst team.
We are hosted on Amazon Web Services and architected for low latency response times to meet the needs of the highest traffic global Internet sites. Typical response time to our API is around 200ms.
Security is essential to everything we do. Among other security measures, all credentials in our database are encrypted and only stored in a salted and strongly hashed format where we have absolutely no way of recovering username and password combinations. Our API calls use a partial hash approach that ensures no password or hash ever leaves your environment. No data submitted to our service is logged and everything in memory is zeroed out at the end of the call. Please see our security overview or contact us for more details.
Our pricing is tailored based on the services required. There are volume discounts that scale based on the total number of calls to our API, along with accounts and domains monitored. Please request a custom price quote today.
Simple RESTful APIs and SDKs make it simple to add Enzoic (formerly PasswordPing) to your site with minimal impact or effort. The typical use case involves wiring calls to our API from your login and change password forms. Please see our API docs for details.
Yes, please request a free trial today.
Block cybercriminals from using stolen credentials for account takeover attacks and credential stuffing.
Experience Enzoic