Enzoic combines the most comprehensive, complete, and actionable threat research data with automated remediation to help you strengthen your security posture.
Experience Enzoic
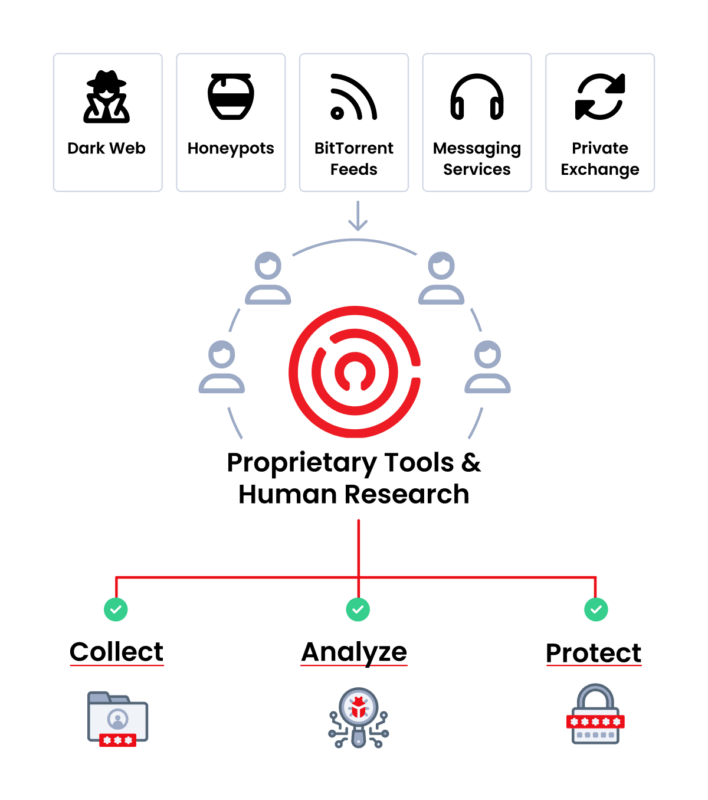
How do we provide our clients with the most current and complete protection?
Our trained analysts scour the public Internet, Dark Web and work with private sources. This human intel is combined with our proprietary tools that automatically intercept and download data 24/7, normalizing and indexing new exposures.
Our credentials and passwords database is updated continuously as new data is obtained, and cleaned from invalid data, duplicated credential records, and data that would lead to unnecessary alert fatigue. This is what makes Enzoic’s threat intel the most current, complete, and actionable.
Learn more658,909
80%
72%
4.1
26,000
PRODUCTS AND SOLUTIONS
Enzoic uses our threat intel database to power products and solutions that give you in-depth protection with no added user friction. What is your biggest challenge?
Blog
Defending Against the Infostealer Threat: Learn how to stymie the flow of attacks and protect your personal information with Enzoic's real-time alerts for compromised data.
Blog
MFA is not invincible. The persistence of compromised credentials as an entry vector for data breaches is a testament to this vulnerability.
Blog
Everyone is talking about AI, but AI-driven security solutions won’t deliver until companies address the basics of defensive security.
Make detecting and eliminating compromised passwords in Active Directory easy with a simple plug-in. Start protecting for free.
Try Now